What is ISO/IEC 62443 standard?
The IEC 62443 is an international series of standards that addresses cyber security for Operational Technology (OT) and the “Industrial automation and control system (IACS)”. This series of standards were created by the committees of the International Society of Automation (ISA) and is the evolution of the ISA99, later called the ANSI/ISA-62443. In 2021 the content of this series was submitted to and used by the International Electrotechnical Commission (IEC) working groups. IEC 62443 has not yet been published in full.
As this standard main objective is to deal with cyber security in OT environments, critical infrastructure and IOT devices, we believe that is the best standard to cover and ensure cyber security in EPES (Electrical Power and Energy System) and critical infrastructures.
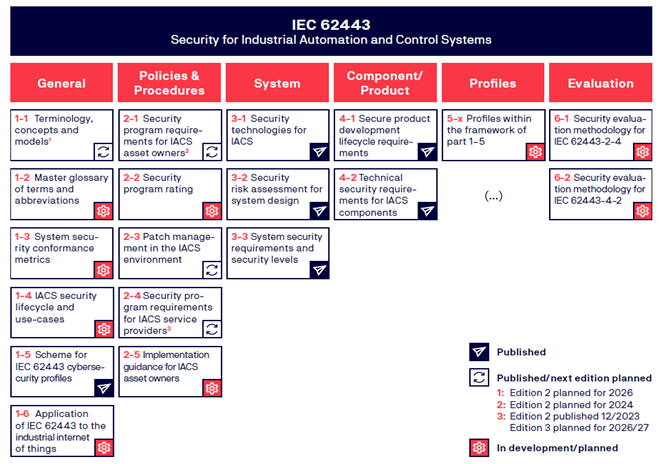
Document Structure
- The IEC 62443 is divided into 4 main layers:
1. General: This section defines the term, definitions, glossaries and concepts used in the IEC 62443 series.
2. Management System: This area defines the requirements for the secure implementation of the management process and the secure integration process of a solution in the process industry.
3. Industrial IT Security (IACS): This area defines the requirements for the security of industrial systems or solutions, e.g. SCADA systems.
4. Embedded safety components: This area defines the requirements for the security of industrial components, e.g. firewalls.

1. General.
1-1 Terminology, concepts and models: Introduces the concepts and models used throughout the series.
1-2 Glossary of terms and abbreviations: Contains a master glossary of terms and abbreviations used throughout the series.
1-3 Metrics for compliance with system security: Describes a series of quantitative metrics consisting of the Foundational Requirements (FRs) and the System Requirements (SRs).
2. Management systems.
2-1 Establishment of an IACS security programme: Describes what is required to define and implement an effective IACS cyber security management system. The standard is based on the ISO27000 series of standards.
2-2 Operation of an IACS security programme: provides specific guidance on what is required to operate an effective IACS cyber security management system.
2-3 Patch management in the IACS environment: provides guidance on the specific topic of patch management for IACS.
2-4 Requirements for the providers of IACS solutions: Specifies requirements that specify a secure integration process for integrators of IACS.
3. Industrial IT Security (IACS).
3-1 Security technologies for IACS: Describes the application of various security technologies in an IACS environment.
3-2 Safety risk assessment and system design: Deals with the assessment of security risks and system design for IACS.
3-3 System security requirements and security levels: Describes the basic requirements for systems security and the security levels.
4. Embedded safety components.
4-1 Life cycle requirements for secure product development: Describes the derived requirements that are applicable to the development of products.
4-2 Technical security requirements for IACS components: Contains sets of derived requirements that provide a detailed mapping of the system requirements (SRs) to subsystems and components of the system under consideration.
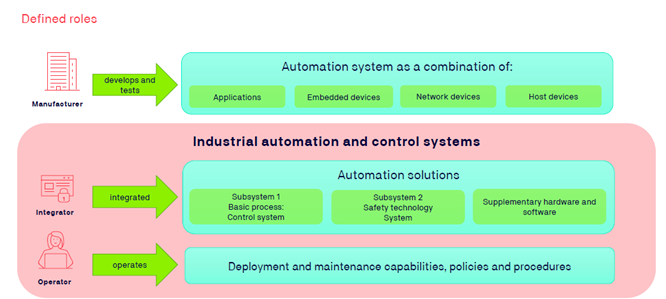
To whom it applies?
- Now that we know the structure and its components, a deeper analysis of some transversal components such as the main roles required for the management of industrial cyber security, as well as the concepts of Security Levels (SL) and Maturity Levels (ML). Focusing on the roles, there are 3 important roles to consider:
• Manufacturers: Manufacturers the product.
• Operator: Uses the product.
• Integrator: Implements the product.
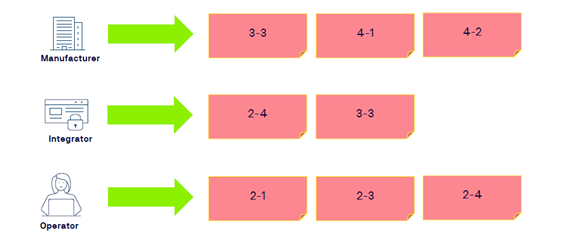
Depending on the role assigned the stakeholder should follow this diagram:
Maturity Levels & Security Levels
As it is mentioned before there are, apart from the roles, another 2 important concepts that are:
Maturity Level are based on the Capability Maturity Model Integration (CMMI) mode.
- Refers to process.
- Consists of 4 Levels.
- The levels build on each other.
- The levels show the optimisation of processes.
The rollers that suit with the maturity levels are:
- Manufacturers
- Integrators
- Operators
The Maturity Levels are classified in the 2-4 and 4-1 standard series.
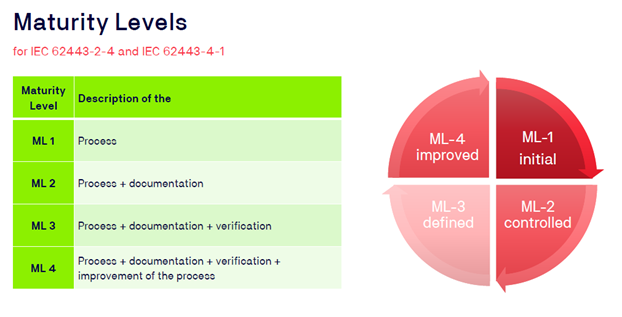
- ML1: Practised incident management process without documentation.
- ML2: Practised incident management process with dedicated policy.
- ML3: Practised incident management process with a dedicated policy with a ticket system.
- ML4: Practised incident management process with a dedicated policy with a ticket system that is regularly reviewed and identified defects are rectified.
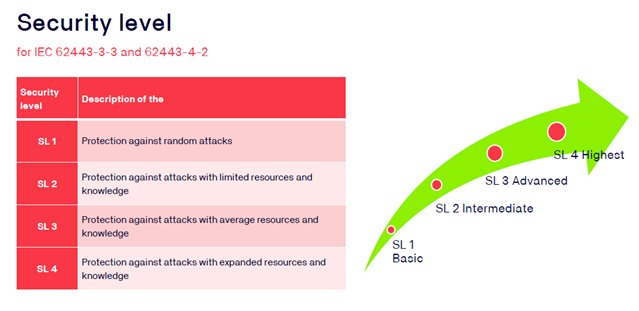
Security Level measures the effectiveness of countermeasures and the safety characteristics of devices and systems.
- Refers to the respective system or component.
- Consists of 4 Levels.
- The levels build on each other.
- The levels show the level of countermeasures and security features.
The rollers that suit with the security levels are:
- Manufacturers
- Integrators
The Security Levels are classified in the 3-3 and 4-2 standard series.
The standard explains various basic principles that should be considered for all roles and activities.
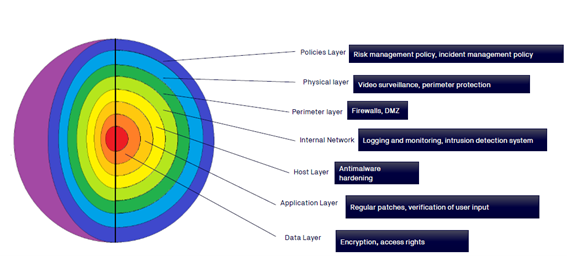
Defense in depth
Defense in Depth is a concept in which several levels of security are distributed throughout the system. The goal is to provide redundancy in case a security measure fails or a vulnerability is exploited (Onion principle).
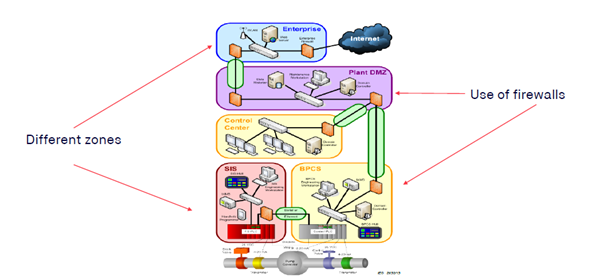
Zones and conduits
Zones divide a system into homogeneous zones by grouping the (logical or physical) assets with common security requirements. The security requirements are defined by Security Level (SL). The level required for a zone is determined by the risk analysis.
Zones have boundaries that separate the elements inside the zone from those outside. Information moves within and between zones. Zones can be divided into sub-zones that define different security levels (SL) and allow enable defense-in-depth.
Conduits group the elements that allow communication between two zones. They provide security functions that enable secure communication and allow the coexistence of zones with different security levels.
Certification process
Going more in depth into the parts of the standard that can be certified mentioned above:
IEC 62443-4-1: Life cycle requirements for safe product development
IEC 62443-4-1 establishes the process requirements for the safe development of products used in industrial automation and control systems. It defines a safe development lifecycle (SDL) that includes the definition of safety requirements, safe design, safe implementation, verification and validation, defect management, patch management and end-of-life of the product. These requirements apply to the developer and maintainer of the product, but not to the integrator or user of the product.
The requirements of the standard are divided into the following topics:
- Safety management
- Specification of security requirements
- Security by design
- Safe implementation
- Secure implementation and validation testing
- Management of security-related issues
- Management of security updates.
IEC 62443-4-2: Technical safety requirements for IACS components
IEC 62443-4-2 is the part of the standard that establishes the technical requirements for the components of a control system (CRs), including the seven fundamental requirements (FR) described in Technical Specification IEC TS 62443-1-1. The fundamental requirements are the basis for defining the safety capability levels of control systems.
The seven fundamental requirements are as follows:
- Identification and authentication control requirements.
- Usage control requirements
- System integrity requirements
- Data confidentiality requirements
- Restricted data flow requirements
- Requirements for timely response to events
- Resource availability requirements
In addition to the technical component requirements (CRs) derived from the listed FRs, this part of the standard also includes product specific requirements for host devices (HDR), network devices (NDR), embedded devices (DER) or software applications (SAR).
IEC 62443-3-3: System security requirements and security levels
IEC 62443-3-3 is an international standard for IACS security that defines detailed technical control system requirements (SRs) associated with the seven foundational requirements (FRs). These requirements are used to define the security levels for IACS systems.
The main purpose of the IEC 62443-3-3 is to provide a consistent and comprehensive set of security requirements for IACS systems. The standard is designed to help organizations protect their critical assets from cyberattacks and ensure the continued operation of their industrial processes.
IEC 62443-2-4: Requirements for the providers of IACS solutions
This part of IEC 62443-2-4 specifies the requirements for safety functions for IACS service providers that they can offer to the asset owner during the integration and maintenance activities of an Automation Solution.
The safety functions offered in aggregate by an IACS service provider are referred to as its Safety Programme. In a related specification, IEC 62443-2-1 describes the requirements for the asset owner’s Safety Management System.
IEC 62443 defines certain requirements for certification:
- Mandatory prerequisite – An IEC 62443-4-1 certificate is required as a prerequisite for the IEC 62443-4-2 certification.
- Optional prerequisite – To carry out an IEC 62443-3-3 certification, it is optional to have a product-related IEC 62443-4-1 certificate as a prerequisite.
