CYBERSECURITY ACT
The EU Cybersecurity Act (CSA), adopted in 2019, represents an important step forward in European Cyber Policy. In order to strengthen the European Union’s stance on cybersecurity, it provides a set of regulations, standards, and guidelines for organizations operating within the EU to ensure a high level of cybersecurity.
Main objectives:
• Strengthening the European Cybersecurity Agency (ENISA):
European Union Agency for Network and Information Security (ENISA) is tasked with supporting Member States in their cybersecurity efforts, providing expertise and promoting high security of networks and information systems within the EU.
• Establishment of a common certification framework: The Act introduces a
cybersecurity certification framework for ICT products, services and processes. This framework aims to harmonise certification processes across the EU, businesses with a unified certification method and consumers with ensuring the cybersecurity of products and services.
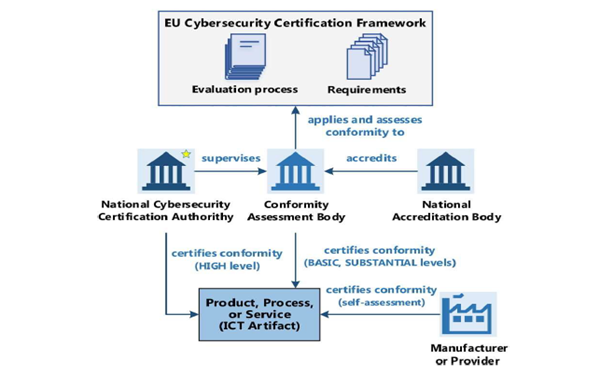
Risk-based approach: By classifying certification schemes into three distinct risk levels – low, medium and high – the Act ensures an efficient allocation of resources.
Stakeholder involvement: The active participation of stakeholders in the certification process is a prominent feature of the Cybersecurity Act. The main players in the industry, consumer representatives, and relevant experts are crucial in shaping and refining certification systems.
Collaboration and Interaction: The emphasis on collaboration is a cornerstone of the Cybersecurity Law.
The Stakeholder Cybersecurity Certification Group (SCCG), established under Article 22 of the CSA, whose overall mission is to support and facilitate strategic issues relating to the cybersecurity certification framework. Upon request, the Group will advise ENISA on strategic issues relating to ENISA’s tasks in the field of market, standardization and cybersecurity certification.
The SCCG is composed of up to 50 members from various organizations, including, inter alia, academic institutions, consumer organizations, conformity assessment bodies, standard developing organizations, companies and trade associations and other membership organizations active in Europe with an interest in cybersecurity certification. The Group includes members appointed from the European Standardization Organizations, such as CEN— European Committee for Standardization, Cenelec— European Committee for Electrotechnical Standardization, ETSI— European Telecommunications Standards Institute. Also involved in the Group are International Standardization Bodies such as the International Organization for Standardization (ISO), the International Electrotechnical Commission (IEC) and the International Telecommunication Union (ITU), the European co-operation for Accreditation (EA) and the European Data Protection Board (EDPB).
Article 52 of the CSA introduces the three levels of assurance of European cybersecurity certification schemes for ICT products and services, as follows:
BASIC
A European cybersecurity certificate or an EU declaration of conformity that refers to ‘basic’ assurance level shall ensure that the ICT products, ICT services and ICT processes for which that EU certificate or declaration of conformity applies meet the relevant security requirements; including security functionalities, and which have been evaluated at a level intended to minimize the Known basic risks of incidents and cyberattacks. The assessment activities to be carried out shall include, at a minimum, a review of the technical documentation. If a revision is not appropriate, substitute evaluation activities with equivalent effect Art. 52.
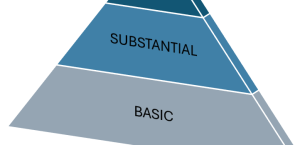
SUBSTANTIAL
A European cybersecurity certificate that refers to assurance level ‘substantial’ shall provide assurance that the ICT products, ICT services and ICT processes for which that certificate is issued meet the corresponding security requirements, including security functionalities, and that they have been evaluated at a level intended to minimize the known cybersecurity risks, and the risk of incidents and cyberattacks carried out by actors with limited skills and resources. The evaluation activities to be undertaken shall include at least the following: a review to demonstrate the absence of publicly known vulnerabilities and testing to demonstrate that the ICT products, ICT services or ICT processes correctly implement the necessary security functionalities. Where any such evaluation activities are not appropriate, substitute evaluation activities with equivalent effect shall be undertaken Art. 52.
HIGH
A European cybersecurity certificate referencing the ‘high’ assurance level should ensure that the ICT products, ICT services and ICT processes for which it is intended are complies with the relevant safety requirements, including the
functionalities, and which have been evaluated at a level designed to minimize the
Risk of state-of-the-art cyberattacks carried out by actors with significant skills and resources. The assessment activities to be carried out shall include, at a minimum, the following: a review to demonstrate the absence of publicly known vulnerabilities; evidence to demonstrate that ICT products, services or processes implement the necessary state-of-the-art security functionalities; and an assessment of their resistance to expert attackers, through penetration testing. Where such assessment activities are not appropriate, replacing the activities with equivalent activities shall be carried out in Article 52.
The Cybersecurity Act as defined in Regulation (EU) 2019/881 introduces a Cybersecurity Certification Framework. This framework provides a unified approach to certifying ICT products, services and processes across the European Union.
At the same time, the EUCC Regulation details the functions, stipulations, duties and organizational functions of the structure of the European cybersecurity certification scheme based on common criteria, ensuring its consistency with the principles articulated by the Cybersecurity Act.
The founding basis of the EUCC is based on the Mutual Recognition Agreement (MRA) of Information Technology Security Certificates developed by the Group of Senior Officials on Information Systems Security (SOG-IS), which uses the Common Criteria along with the procedures and documentation established by the group. The Technology Security Assessment, recognized as ISO 15408, is a recognized benchmark for IT security assessment. This partnership underlines the Union’s determination to synchronize its cybersecurity certification methodology with the recognized standards.
In the context of the EUCC, the vulnerability assessment subset of the Common Criteria, called AVA_VAN, is employed. This subset consists of five core components that are the main tools for examining vulnerabilities inherent in ICT products. These correlate directly with the assurance levels described in the EUCC Regulation.
In addition, the Cybersecurity Act requires that any entity applying for EUCC certification must provide comprehensive documentation clarifying the intended application of ICT product and the inherent risks. Such a directive ensures a thorough security assessment, prerequisites and a holistic risk assessment.
The evaluation criteria stipulated for ICT products require that any product under certification will be evaluated against several parameters. These include the components of the standards referred to in Article 3, the security assurance prerequisites covering vulnerability assessment, independent assessment and rectification of defects set out in the assessment standards, and the risk levels linked to the designated use of ICT commodities in accordance with Articles 51 and 52 of the Cybersecurity Act. In addition, products shall adhere to the relevant state-of-the-art documents listed in Annex I. The EUCC Regulation stresses the importance of conformity assessment bodies and cybersecurity certification authorities by stating that products adhere to the Benchmark. When a product differs from a contemporaneous document, it is imperatively justified, and the competent authorities must be informed. In addition, the products classified in an armored segment by a ratified protection profile are evaluated based on the elements of the profile.
A certification body must be accredited in accordance with ISO/IEC 17065 by the National Accreditation Body for the “substantial” and “high” level of assurance. In addition to accreditation in accordance with Regulation (EC) No 765/2008, conformity assessment bodies must comply with specific requirements to ensure their technical competence for the assessment of cybersecurity requirements according to the EUCC’s ‘high’ assurance level, which is confirmed by an ‘authorization’. To support the authorization process, ENISA should develop and maintain guidance and publish it following its approval by the European Commission’s Cybersecurity Certification Group. Finally, in scenarios involving product evaluation, the EUCC Regulation underlines the importance of synergies between different Information Technology Security Assessment Facilities (ITSEFs). The technical competence of an ITSEF should be assessed by accreditation of the testing laboratory in accordance with ISO/IEC 17025 and supplemented by ISO/IEC 23532-1 for the full set of assessment activities that are relevant to the assurance level and specified in ISO/IEC 18045 in conjunction with ISO/IEC 15408. In cases where an underlying ICT product has been previously assessed, the information is shared between the ITSEF that carried out the initial assessment and the ITSEF that carried out the composite product assessment.
A certification process diagram:
The EU Cybersecurity Act 2019 is considered a legislative milestone that underlines the EU’s commitment to improving its cybersecurity framework. By strengthen ENISA, introduce a harmonized certification framework, and promote by working together with the various stakeholders, the Act ensures a robust and unified approach to cybersecurity across the European Union.
https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-act
