Cyber Resilence Act
Cyber Resilience Act (CRA) of 2023, is a landmark regulation aimed at bolstering the cybersecurity posture of digital products and services. This comprehensive piece of legislation establishes a robust framework for manufacturers, distributors, and consumers, ensuring a more secure and resilient digital landscape.
Specific objectives of CRA: ensure that manufacturers improve the security of products with digital elements since the design and development phase and throughout the whole life cycle; ensure a coherent cybersecurity framework, facilitating compliance for hardware and software producers; enhance the transparency of security properties of products with digital elements; enable businesses and consumers to use products with digital elements securely.
Design and Development:
- Security-by-Design: Digital products must be designed and developed with security in mind from the outset, incorporating robust security measures throughout the development process.
Vulnerability Management:
- Vulnerability Identification and Remediation: Manufacturers must establish a proactive vulnerability management program to identify, assess, and promptly address vulnerabilities in their products.
Software Updates:
- Regular Security Updates: Manufacturers must provide regular security updates to address newly discovered vulnerabilities and maintain the overall security posture of their products.
Security Labelling:
- Transparency and Informed Consumer Choices: Products must be labelled with clear and transparent information regarding their cybersecurity level, enabling consumers to make informed choices based on their risk tolerance.
Additional Provisions:
- Security Incident Disclosure: Manufacturers are mandated to disclose security incidents to the relevant authorities, enabling timely and coordinated responses to
cyber threats.
- Point of Contact for Security Researchers: Manufacturers must provide a designated point of contact for security researchers, facilitating collaboration and fostering
responsible vulnerability disclosure practices.
- Cooperation with Law Enforcement: Manufacturers are required to cooperate with law enforcement agencies in the investigation of cyberattacks, contributing to the effective prosecution of cybercriminals.
Impact and Implications:
- The Cyber Resilience Act is poised to have a profound impact on the cybersecurity landscape, bringing significant changes for manufacturers, distributors, and consumers.
For Manufacturers:
- Enhanced Security Posture: The act mandates a comprehensive approach to security, compelling manufacturers to integrate security into every stage of product development and maintenance.
- Increased Transparency: The requirement for security labelling necessitates transparency and accountability, fostering trust among consumers.
For Distributors:
- Product Information and Compliance: Distributors must ensure that products are accurately labelled and comply with the act’s requirements, ensuring informed
consumer choices and adherence to regulatory standards.
For Consumers:
- Empowered Decision-Making: Clear security labelling empowers consumers to make informed choices based on their security needs and risk tolerance.
- Increased Protection: The act’s focus on security enhancements and vulnerability management translates into a more secure digital environment for consumers.
Critical Products subject to CRA Provisions:
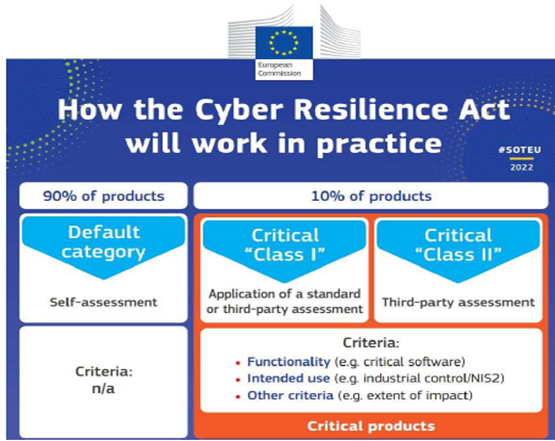
|
CRITICAL PRODUCTS WITH DIGITAL ELEMENTS |
|
CLASS II |
|
Operating systems for servers, desktops, and mobile devices |
|
Hypervisors and container runtime systems that support virtualised execution of operating systems and similar environments |
|
Public key infrastructure and digital certificate issuers |
|
Firewalls, intrusion detection and/or prevention systems intended for industrial use |
|
General purpose microprocessors |
|
Microprocessors intended for integration in programmable logic controllers and secure elements |
|
Routers, modems intended for the connection to the internet, and switches, intended for industrial use |
|
Secure elements |
|
Hardware Security Modules (HSMs) |
|
Secure cryptoprocessors |
|
Smartcards, smartcard readers and tokens |
|
Industrial Automation & Control Systems (IACS) intended for the use by essential entities of the type referred to in [Annex I to the NIS2 Directive], such as programmable logic controllers (PLC), distributed control systems (DCS), computerised numeric controllers for machine tools (CNC) and supervisory control and data acquisition systems (SCADA) |
|
Industrial Internet of Things devices intended for the use by essential entities of the type referred to in [Annex I to the NIS2 Directive] |
|
Robot sensing and actuator components and robot controllers |
|
Smart meters |
In the case of OT equipment, it is recommended to create a compatibility mechanism based on the already adopted framework of European industrial safety standards (EN IEC 62443), including the associated available IACS certification schemes operated by accredited agents of the European Conformity Assessment Bodies (CAB). The level of responsibility of the manufacturer with respect to the supply chain of its products should be specified in terms of due diligence requirements.
The Cyber Resilience Act of 2023 represents an important step forward in safeguarding the digital world. By establishing a comprehensive framework for cybersecurity, the law addresses the changing cyber threat landscape and empowers manufacturers, distributors, and consumers to play a proactive role in improving digital resilience. The implementation of the law is expected to bolster consumer confidence, strengthen the digital economy, and contribute to a safer and more resilient digital future.
Latest updates on CRA
In recent months there have been significant developments regarding the Cyber Resilience Act (CRA).
On March 12th, the European Parliament sanctioned the Cyber Resilience Act (CRA), delineating cybersecurity requisites for “products with digital elements” (PDEs) introduced in the EU market. PDEs encompass a wide array of hardware and software, including antivirus software, VPNs, smart home devices, connected toys, and wearables. The endorsed text mirrors the compromise version between the Parliament and the Council from December 2023.
Primary obligations under the CRA fall upon PDE manufacturers, mandating the implementation of essential cybersecurity requirements, conducting conformity assessments, and promptly notifying competent authorities about identified vulnerabilities and serious cybersecurity incidents. Non-compliance may attract substantial fines, potentially reaching up to the higher of €15 million or 2.5% of global turnover.
4 April 2024 – Paper: “Cyber Resilience Act (CRA) Requirements Standards Mapping” – from ENISA and the European Commission’s Joint Research Centre.
The Cyber Resilience Act (CRA) proposal covers all products with digital elements put on the market which can be connected to a device or a network, including their building blocks (i.e., hardware and software), and encompassing also solutions provided in a Software as a Service (SaaS) fashion if they qualify as remote data processing solutions, as defined by Article 3(2) of the CRA proposal.
The CRA proposal provides two sets of essential requirements:
- Product cybersecurity requirements in Annex I, Section 1 of the CRA proposal.
- Vulnerability handling process requirements in Annex I, Section 2 of the CRA proposal.
These requirements should be the subject of a standardisation process by the European Standardisation Organizations (ESOs) to express them in the form of specifications in harmonised standards.
This report details the available standardisation outputs on the cybersecurity of products (hardware and software products, including hardware and software components of more complex products) carried out mainly by ESOs and international Standards Development Organizations (SDOs). Specifically, the study aims at presenting a mapping of the existing cybersecurity standards against the essential requirements listed in Annex I of the CRA proposal, along with a gap analysis between the mapped standards and the requirements.
